The forensic analysis of mobile devices in the past decade has kept pace with the ever-changing technologies and services provided to consumers. Data extraction and analysis techniques have evolved and made significant improvements to investigators’ abilities to solve crimes. Data from devices such as smartphones and tablets is now as complex as traditional computer forensics, but the value is all the greater for being portable and part of everyday life.
Mobile device forensics has evolved significantly in recent years, with innovations in techniques and tools that allow investigators to extract and analyze data from smartphones, tablets, and other portable devices. These advancements have become increasingly relevant in criminal investigations, providing valuable insights into various crimes.
Key Techniques and Advancements
When conducting an investigation, the first challenge is to gather the relevant data. Physical extraction from a device using specially designed hardware and software is the first step. Software for decrypting a device and accessing the content is required for direct access to the device’s hardware to extract data and is often used in cases where the device is locked or damaged. JTAG (Joint Test Action Group) and SPI (Serial Peripheral Interface) are the least invasive processes and are usually sufficient for locked, damaged, or unique operating systems. For more difficult situations, Chip-Off techniques are used to draw information directly from the device’s flash memory however, they are more invasive and potentially destructive to the device.
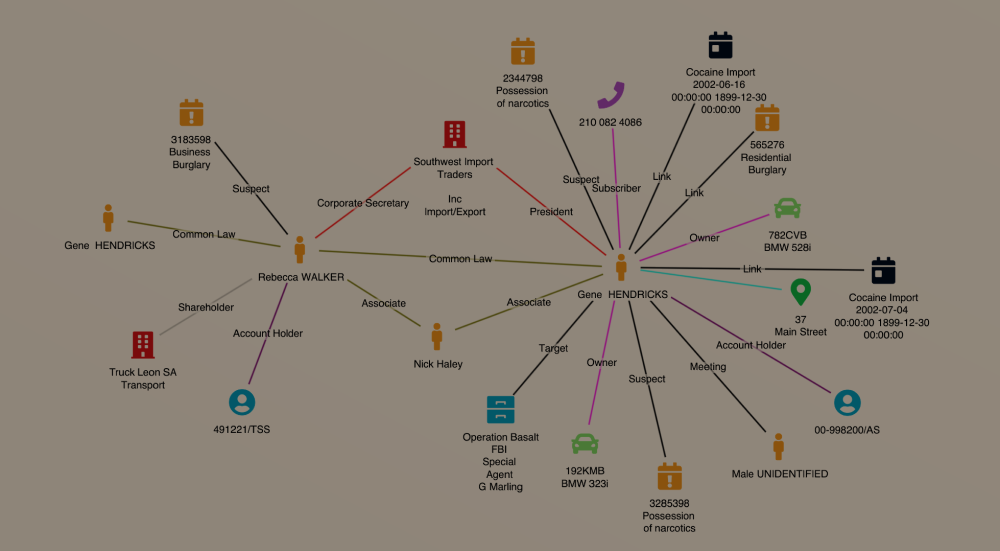
Logical data extraction is also important to investigators for file system analysis to identify and extract relevant data, such as contacts, messages, call logs, and photos. These elements are essential in investigations for establishing connections amid profiles, phone numbers, and individuals beyond the identification of a perpetrator.
Remotely stored data in cloud-based services and databases can also extracted through the device from these services, with the benefit of internally saved passwords and registered connections. Once data is retrieved, analysis needs to be conducted. Advancements in forensic tools can now recover deleted files and hidden data, and search for specific keywords. They can now establish a timeline of events based on timestamps and even geolocation if these services are activated on the device by the user. Analytical products will show the who, when, and where of activities (passive or active) that the device was present or engaged in. While a device does not yet provide proof of the actor, it does provide valuable circumstantial evidence that the device user was also the actor of the events recorded in the data. Valuable information can be derived from network analysis, such as call data records, and forensics on the installed applications.
Experts in digital forensics have developed more sophisticated methods to bypass device locks and extract data from encrypted devices, even when using strong passwords or biometric authentication. Cloud-based platforms have become more prevalent because they enable remote analysis of devices and access to data stored in cloud services. Because of this, forensic tools have been adapted to handle “over-the-air” updates, which can overwrite or delete data, making it crucial to extract data before updates occur.
Data analysis tools have been improved by the adoption of recent pronounced advancements in artificial intelligence and machine learning. AI algorithms have been integrated into forensic software to automate tasks, such as identifying patterns, classifying data, and extracting relevant information.
New solutions for emerging technologies have recently been developed in response to the exponential growth of internet-connected devices, such as home appliances and electronics, smart speakers, and wearable devices. A person’s daily activities, health data, and location can provide clues to investigators of patterns of behavior; when suspects may be at home or work, and locations they frequent.
The most important advancements of technologies in this field have been the improvements in capabilities to extract data from encrypted messaging apps, such as WhatsApp, Telegram, and Signal, by leveraging vulnerabilities or exploiting weaknesses in the underlying protocols.
Ethical Considerations in Mobile Device Forensics
Mobile device forensics, while a powerful tool for law enforcement, raises significant ethical concerns due to the personal nature of the data stored on these devices. These considerations include privacy, data protection, and international cooperation. There is increasing emphasis on ethical considerations in mobile device forensics, ensuring that investigations are conducted by following privacy laws and regulations. Collaboration among law enforcement agencies worldwide is essential for addressing cross-border crimes involving mobile devices and establishing international standards and best practices.
Privacy and Data Protection
In the United States, the Fourth Amendment of the U.S. Constitution protects individuals from unreasonable searches and seizures. This applies to digital evidence, including data stored on mobile devices. In the European Union and Great Britain, GDPR (General Data Protection Regulation) has within the past 10 years been strengthened to protect individuals from breaches of privacy and cross-border limitations on the sharing of citizens’ personal information.
Favorably, ethical standards have been established to protect individuals from unfair, illegal search and seizure, and to maintain privacy during digital forensic investigations. Forensic investigators should only extract and analyze relevant data to the investigation, avoiding unnecessary intrusion into a person’s privacy. Retaining data beyond the necessary timeframe can pose privacy risks, especially when dealing with sensitive information. Limits on the length of time and a list of valid reasons to retain data are included in data privacy laws. To maintain individual freedoms, informed consent obtained from individuals before conducting forensic analysis is crucial, especially when dealing with non-suspects. When conducting forensic investigations that involve data stored in other jurisdictions, it’s essential to comply with international data transfer laws and regulations, such as the General Data Protection Regulation (GDPR).
Chain of Custody
Maintaining the integrity of evidence is paramount in forensic investigations. This includes ensuring the chain of custody is unbroken and preventing tampering or unauthorized access to the device. Proper documentation of all steps involved in the forensic process is essential to ensure the admissibility of evidence in court.
Some forensic techniques can be destructive, meaning they may damage or permanently alter the device. This should be avoided, if possible, especially when dealing with devices that may contain valuable data for the individual. Forensic tools and techniques should be validated and regularly updated to ensure their accuracy and reliability.
Forensic experts who testify in court must have the necessary qualifications and experience to provide reliable and unbiased testimony. Expert testimony should be clear, concise, and avoid technical jargon that may confuse the jury.
By addressing these ethical considerations, law enforcement agencies can ensure that mobile device forensics is conducted responsibly and lawfully, protecting the rights of individuals while effectively investigating crimes. As technology continues to advance, so too will mobile device forensics techniques. Law enforcement agencies must stay updated on the latest developments to effectively employ this powerful tool in criminal investigations.